Internet Safety 2011
Tuesday, 7 June 2011
Internet Safety Questionnaire
Internet Safety qualification, consisting of a single Unit at
Intermediate 1. This qualification was aimed mainly at secondary school
and college students and has seen a substantial uptake from these groups.
However, there have been significant changes in Internet use since 2006,
particularly the increased use of Social Networking and the associated
dangers. A minor revision of the qualification was undertaken in late
2010, prior to having it accredited on QCF for use in England and Wales.
SQA is now proposing to carry out a major revision of the unit as used
in Scotland. I have been commissioned by them to research opinions
regarding the content of the revised qualification. To this end I would
be grateful if you could take some time to answer the following
questions at your earliest convenience. The questions should take only
a few minutes to answer. Your responses will have a major impact on
shaping the revised qualification.
The questionnaire can be found at: http://www.surveymonkey.com/s/9SBZPR7
Once the results have been analysed they will be published on the SQA Computing
blog and other sources.
Thank you for your cooperation. If you have any queries, or other
comments to make, or wish to suggest anyone else who ought to receive
this questionnaire, please email ted@hastings.nu.
Monday, 14 February 2011
Thank you
Please contact Caroline Douglas if you want to know more about the "proper" course (the full Internet Safety qualification).
We'd like to hear about your experience of doing this course using Twitter/Blogger so please leave feedback via the comment facility.
You might want to stop following this Twitter account now, since we will not use it again, but
you can follow the SQA Computing team on Twitter here if you want to keep up to date with the full range of Computing/IT qualifications currently available or being developed.
Friday, 11 February 2011
Reliability of Information
 When people are searching online for information they often simply accept the first few sites brought up on a search made using Google or another search engine. But unfortunately, not all information found online is accurate. Web pages may be written by someone with little or no knowledge of the subject area, they may be designed to encourage you to buy a specific product or they may be biased in favour of someone’s opinions, whether or not these reflect the facts.
When people are searching online for information they often simply accept the first few sites brought up on a search made using Google or another search engine. But unfortunately, not all information found online is accurate. Web pages may be written by someone with little or no knowledge of the subject area, they may be designed to encourage you to buy a specific product or they may be biased in favour of someone’s opinions, whether or not these reflect the facts. Major information sites like Wikipedia are generally accurate when dealing with factual or technical subjects, including Computing topics, but they may be less accurate when dealing with subjects where opinions play an important role, for example current or historical events or political topics.
You should always evaluate the quality of information found on website using five criteria:
- Scope of Coverage: to what extent does the site explore the topic?
- Authority: does the information come from a source which is known to be reliable?
- Objectivity: does the site cover a range of views, or does it simply express the author’s bias or opinions?
- Accuracy: is the information correct? How has this been checked? Can the same information be obtained from other sources?
- Timeliness: is the information current, or was it published some time ago? When was the website last updated?
You can obtain further information about each of these criteria at:
http://virtualchase.justia.com/quality-criteria-checklist
This site also contains plenty of other useful information about checking the reliability of websites.
Uploading Files
 There is only one useful piece of advice that can be given about uploading files – unless you are absolutely certain the file you are uploading is your own property: DON’T DO IT.
There is only one useful piece of advice that can be given about uploading files – unless you are absolutely certain the file you are uploading is your own property: DON’T DO IT. There is no problem with uploading photos you have taken yourself to Flickr, or videos you have made yourself to YouTube, but you should never upload content that belongs to someone else.
When you buy an album or a video, you only own that single copy – you don’t have the right to upload it to file-sharing sites.
Copyright holders tend to take much stronger action against uploaders than against downloaders, as a single upload can lead to thousands or even millions of downloads.
In November 2010 a Swedish appeals court upheld the copyright convictions of three men behind The Pirate Bay, a popular file-sharing site. They were fined millions of dollars and sentenced to years in jail.
In the same month a Minneapolis woman, Jammie Thomas-Rasset, was found guilty of illegal song file sharing, and ordered to pay the Recording Industry Association of America (RIAA) $1.5 million. The RIAA claimed that she shared more than 1,700 songs on a file-sharing site, but it sued over only 24 of them.
Using a BitTorrent client to download files can be a particularly dangerous activity as anyone who downloads is also uploading, due to the way the BitTorrent software works.
Thursday, 10 February 2011
Facebook Security
At the bottom of every page on Facebook, there's a link named Privacy. Clicking this will take you to a page entitled “Controlling how you share” which provides useful advice on Facebook’s security settings and has a link which allows you to Edit your privacy settings.
Facebook makes some information, including your name, profile picture, gender and networks available to everyone and you cannot make this information private. You can use the Preview my profile button on any privacy settings page to see how your information appears to others.
Be careful about allowing people to become your friend on Facebook. Once you have accepted someone as a friend they can access any information that you have marked as viewable by friends. Remember that you can remove friends at any time and that you can restrict people’s access to your profile by making them limited friends.
Facebook also shares information with websites and apps, including search engines. You can remove any apps you don't want to use or turn off platform completely. If you do this you won't be able to use any platform apps or websites and Facebook won't share your information with them.
Internet Explorer Security Settings
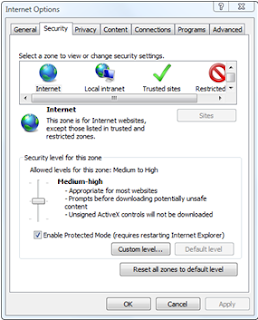 You can change Internet Explorer’s security settings as follows:
You can change Internet Explorer’s security settings as follows: 1. Open Internet Explorer by clicking the Start button at the bottom left of the screen and then clicking Internet Explorer.
2. Click the Tools button, and then click Internet Options.
3. Click the Security tab.
Internet Explorer assigns websites to one of four security zones: Internet, Local intranet, Trusted sites, or Restricted sites. The zone to which a website is assigned determines the security settings used for that site.
There are 5 levels of security setting available for each Internet Explorer security zone, but not all levels are available for all zones:
- Low
- Medium-Low (default for Local Intranet)
- Medium (default level for Trusted Sites)
- Medium-High (default for Internet or unclassified sites)
- High (default for Restricted Sites)
Browser Safety and Security Settings
 Web browsers, which allow you to view the content of web pages, are now amongst the most commonly-used computer applications. Most people use Internet Explorer (which comes preinstalled on Windows systems) or Firefox (which is available in Windows, Mac and Linux versions), but there are other alternatives including Opera and Chrome.
Web browsers, which allow you to view the content of web pages, are now amongst the most commonly-used computer applications. Most people use Internet Explorer (which comes preinstalled on Windows systems) or Firefox (which is available in Windows, Mac and Linux versions), but there are other alternatives including Opera and Chrome.Browsers can leave you and your system open to danger. Most browsers allow you to run small downloadable applications, such as Java applets or ActiveX controls.
 Unless you are very careful about what you allow, these can wreak havoc on your system by deletion or damaging files or by installing malware of some sort.
Unless you are very careful about what you allow, these can wreak havoc on your system by deletion or damaging files or by installing malware of some sort.
Your browser may allow you to visit sites which will automatically download malware, such as viruses or spyware. It may also allow you to visits sites with objectionable, or even illegal content, such as pirated software or video files, which may themselves be infected with malware.
Fortunately, browsers generally provide a range of security settings, which can alleviate or eliminate most major security problems. Over the next few pages we’ll look at how you can configure the security settings in Internet Explorer and Firefox.
